Obstacles to security clarity

If you’re wondering why your security efforts don’t seem to pay off that much in terms of actually securing your system, you’re not alone. Security professionals, and company leaderships, feel ill equipped to manage security, and have been feeling this way for a long time.
Year after year, we see data breaches in companies with plenty of information security funding. It’s not a secret that well-funded security teams also have a hard time implementing effective security controls, and an even harder time doing effective security testing of said controls. Even when these controls have been known for a very long time and are fairly easy to implement. Teams lacking funding are usually doing even worse. Too many times easy to implement controls are failing - like managing what outbound ports are allowed, tuning the IDS to detect obvious hacking, or even ensuring the antivirus is turned ‘ON’. Furthermore security teams are surprised when they learn they fail such simple security controls. On the other hand, many of these same organizations don’t have any problems passing a security audit.
This post will point out many of the hinders to effective cyber security, while outlining the remedy for some of the pains associated with securing an organization’s IT systems.
Sources of confusion

NIST 800-53 anyone?
Let’s go over the main reasons why our attention isn’t geared towards solving the basics of information security.
1. We’re compliant, not secure
Being compliant simply means auditors found you to have sufficient controls in place. In practice, this means that someone, with even less understanding of your systems than the security team, tries to figure out if it is secure. For the most part, this becomes an exercise in creating paperwork which says “we do this, and we do that”. At the end the auditor will usually give their blessing, along with a list of things they think would improve the system.
The problem with audits is that it is in everyone’s interest to pass a security audit; both the auditor and the employees of the organization under audit have a financial incentive to pass the audit. And so the incentive for passing the audit is far stronger than finding the truth. This is why audits do not give clarity on an organization’s security - and it usually only creates more paperwork.
2. We’re caught up in the hype
We spend lots of time and resources focusing on specific vulnerabilities which are oftentimes hyped up in the news. The fact is that you can spend days fixing ONE vulnerability, or you can put in place basic security controls that mitigate that one vulnerability, plus hundreds of other vulnerabilities. This happens all the time. We’re playing whack-a-mole with vulnerabilities instead of handling vulnerabilities holistically. This exact same thing happens in terms of other types of security hypes - like shiny new security tools or training promising to solve our problems once and for all.
3. We’re slow
There is another problem that might be even more striking in certain cases - security teams work like development teams worked 10 years ago: slow iterations, very little testing (except for patch management). And the feedback loop relies on real failures and an occasional audit.
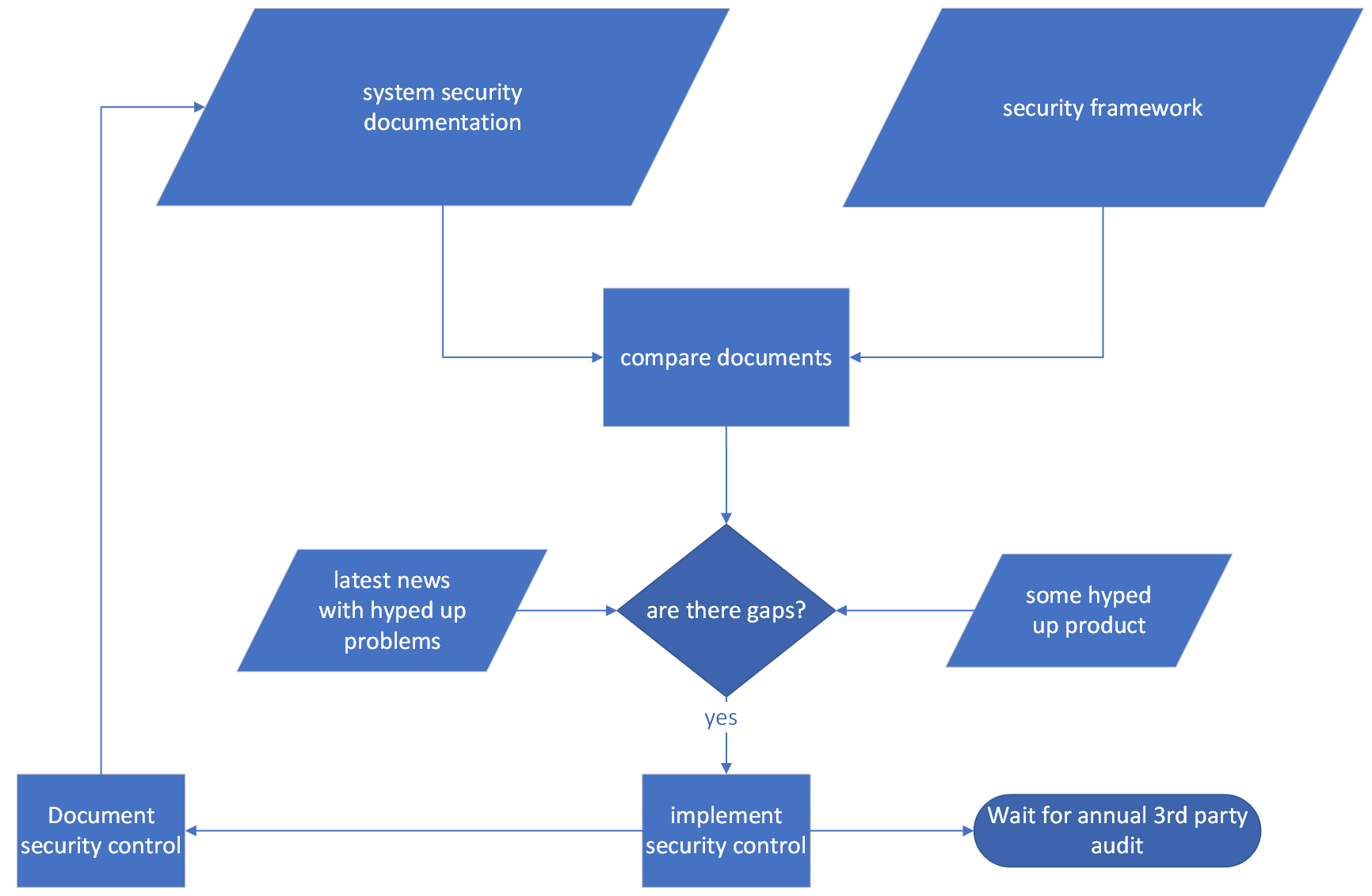
Typical compliance- and hype-driven process
Bad results over time
This, in turn, leads to a significant lag time in effective security controls implementations — from small business to large enterprises and government organizations. And no clarity into what works?
Solution: Test Driven Security
The solution is to test important security controls as quickly and often as possible. This is what’s referred to as test driven security. If you’re interested in learning more, read on the method of test driven security, or check out guides on how to actually do the testing, starting with network tests and IDS tests.
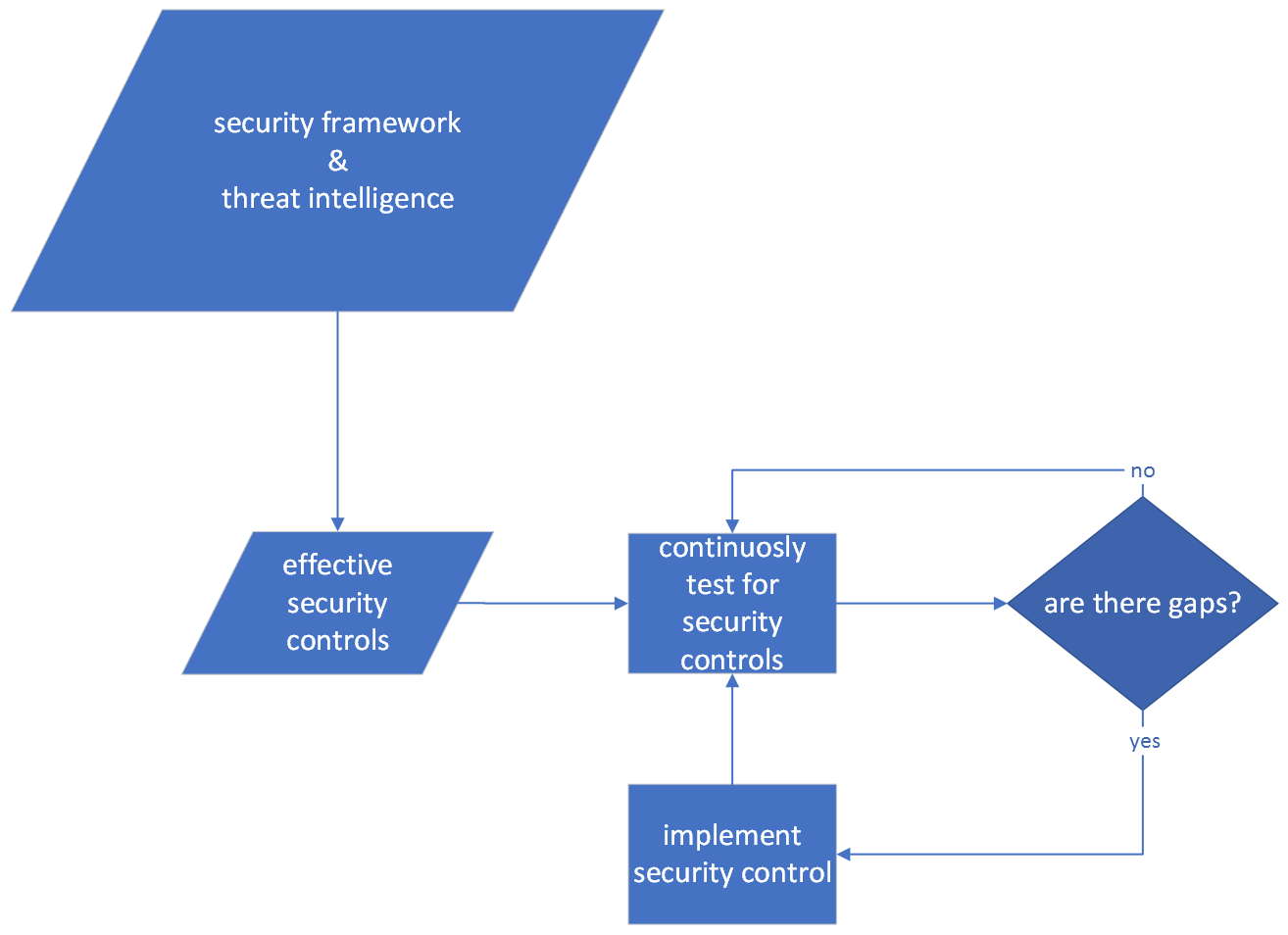
Test driven security
In the next article we’ll take an in-depth look at test driven security.
If you like this article, please share using the buttons below!
Thanks!
