Test driven security

Have you ever asked yourself if all your hard work and investments in security will pay off in stopping a cyber attack? You probably have, especially if you’re in IT or in a leadership position. As a security professional for many years, I found myself asking this question a lot. I also asked others the same question. The answers I got was usually “I hope so” or “I think so”. Usually the answer was followed up with “I wish I knew”.
The need to know
The current state we’re in is that information security professionals know –that they don’t know– how secure their own systems are, and feel I’ll equipped to manage security. This extends to how private citizens’ view companies’ ability to manage security. There is little confidence accross the board.
The proven way to get more confidence is to test if what we’re doing works, or if we need to improve on something. This line of thinking ties into the methodology of failing fast.
It’s like most other things in life - such as sports, personal health, and dating: You need to test to know.
We’re effective when we have clarity on our security gaps
When we understand we have a significant security gap, we are able to put resources into fixing the problem: IT organizations, which usually are fairly stagnant, summon the troops, poor in resources, and quickly fix problems to reduce risk. Unfortunately this usually happens when news break about some exploitable vulnerability, after a annual penetration test, or when the organization fails a compliance requirement.
The main problem with this type of learning is that it is reactive and unstructured. In addition, the information we get is sometimes irrelevant and over emphasized relative to other gaps, which results in a slow progression towards clarity. We need to find ways to learn about what is relevant to us, and to do it as fast as possible. This can be achieved through methodic testing of relevant security controls and then analyzing the results.
Solution: Test Driven Security
What gets measured gets done —supposedly not Peter Drucker after all.
What we need in order to gain clarity, quickly, is to perform tests, and get quick and actionable feedback. This is a much better way than dreaming up ideal architectures, being overwhelmed by hundreds of pages of compliance documents, or worrying about the latest security news.
Testing requirements:
- Know what is critical to test.
- Know how to test.
- Test often.
Build, test, fix, repeat:
Similar to test driven development; a security team chooses the most important/effective controls which must not fail, writes tests that verifies whether they do - then whatever fails, is improved. Instead of slow and expensive iterations, we can get short and affordable iterations, with actionable feedback loops. Like below:
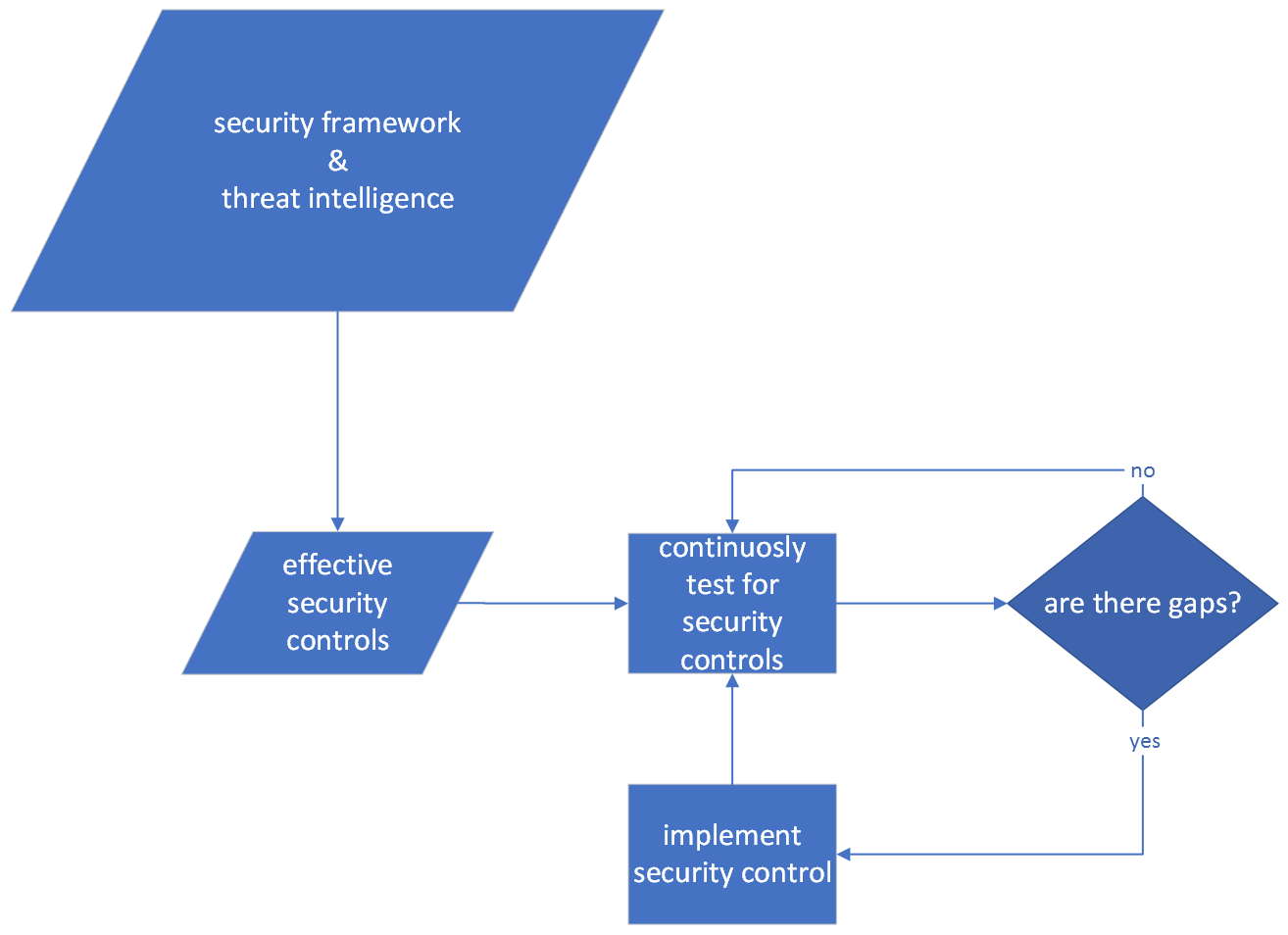
Test driven security
Security controls requirements:
- Effective.
- Easy(ish) to implement.
- Measurable.
If at some point we have met all of these criteria, we could expand the scope to include controls that are either less effective, or harder to implement. We still need them to implement the controls in such a way that they can be measured.
In the next articles we’ll take a look at how we can run test driven network security and test driven intrusion detection and monitoring
If you like this article, please share using the buttons below!
Thanks!
